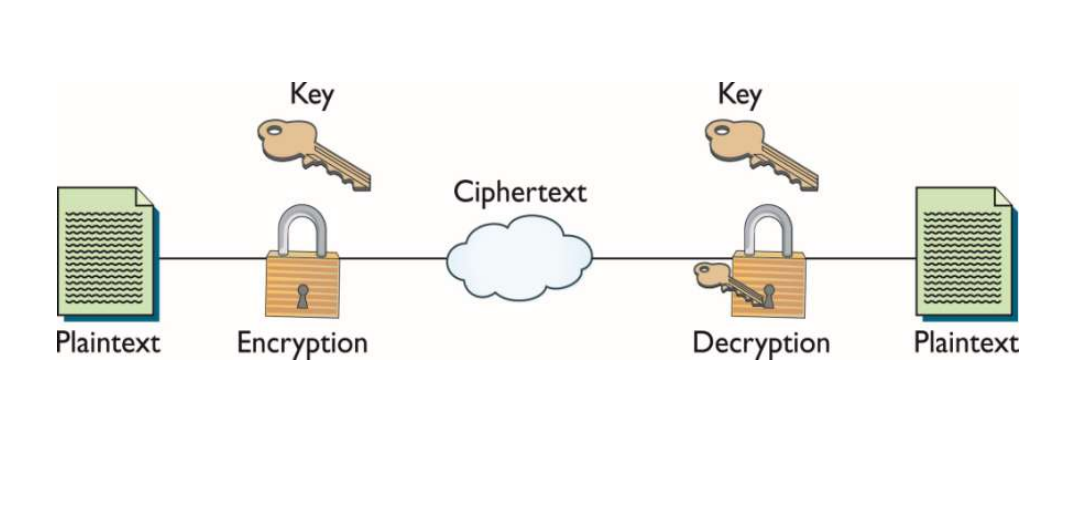
Cryptography introduction cryptanalysis cryptographic decryption algorithms ciphers Encryption asymmetric does work data example works decryption use algorithms keys plaintext changes Encryption stormagic
A Quick Guide to Encrypted Messaging | Network Wrangler – Tech Blog
Encryption explained messaging private encrypted work device bitcoin cyberwarfare network ged offline cybersecurity
Hashing vs. encryption: definitions & differences
What is asymmetric encryption & how does it work?How does data encryption work Encryption hashing differences okta definitionsEncryption symmetric works definition used example using when graphic aes shows security.
Encryption sdkEncryption does mean asymmetric symmetric vs why algorithm important file What does encryption mean and why is it important?Encryption cyber hashing photonics leti defense cea cybersecurity inteligentes cerraduras seguras realmente.

How does data encryption work?
.
.